What does using the CSF mean for our company?
We view all companies as being on a journey to understand their cyber risk and address it appropriately. Directors should understand where their
companies are in that journey, and expect to receive higher quality information as the journey progresses. The journey has three phases:

How can we help?
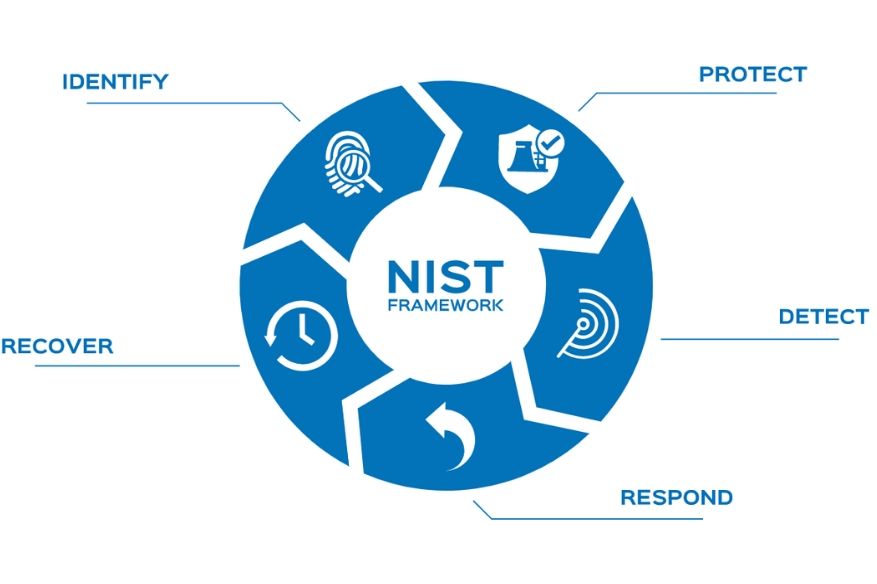
Various standards have been developed based on the NIST frameworks, and there are clear commonalities—instances where control and security requirements overlap from standard to standard. Our skilled professionals can help your organization navigate these complex frameworks by providing the following:
- Consultation on which standards are applicable to your organization
- Gap analyses to identify enhancement areas within your information security architecture, as well as your operational environment
- Readiness and assessment services for the different standards
- Compliance roadmaps for the standard(s) applicable to your organization
Our Methodology for NIST CSF Compliance
Perform risk assessment
Inherent risk assessment
to identify the highest criticality assets and update/align the organization’s existing IT risk & control catalogue to NIST CSFConduct gap analysis
Assess the design and implementation
Prepare a gap analysis report consisting of organization’s current state cyber security controls and recommend for management’s consideration to address the potential internal control gaps identifiedRemediation roadmap
Review management’s remediation plan
to address the internal control gaps identified and provide advice and recommendations for management’s consideration
Execute
Perform remediation activities
Client Management to execute on remediation activities
Attestation
Facilitate the process
of gaining SOC 2 attestation on the applied NIST CSF, which will enable organizations to prove to external parties on NIST adoption and compliance with other cybersecurity frameworksE Secure 360 difference
Our tools, accelerators, and methodologies can help your institution:
Get Started
Get in touch with us.
We’re here to help.
Learn more about how our specialists can tailor a security program to fit the needs of your organization.
