Vulnerability Assessment of SCADA and Industrial Control Systems
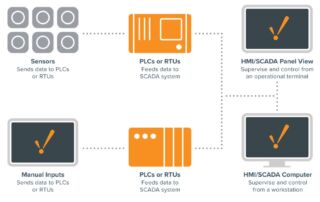
What is SCADA? Supervisory Control and Data Acquisition (SCADA) is a system of software and hardware elements that allows industrial organizations to: Control industrial processes locally or at remote locations Monitor, gather, and process real-time data Directly interact with devices such as sensors, valves, pumps, motors, and more through human-machine interface (HMI) software Record events into a log file SCADA systems [...]
Raise of Phishing attacks
The number of coronavirus-related email attacks has increased by 667 percent since the end of May 2021, according to a cybersecurity threat report published by E Com Security Solutions. Many organizations and companies experience changes in their working conditions due to the covid-19 pandemic. This shift has increased remote activities, such as teleworking. Teleworking furthers the reliance on email for [...]
Cyber Security tips for work from home
Due to the COVID-19 pandemic, most of the organizations globally moved their employees to a remote mode that increased the risk of security threats and vulnerabilities that lead to leaks of critical data and core information systems breaches. It is challenging enough for cyber security teams to constantly defend an organization’s networks from cybercriminals, and malicious insiders when the workforce [...]
AI in Network Penetration testing
Penetration testing is a vital component in the field of cyber security. To be theoretical it should be placed in the forefront for any security tragedy. Now let’s look at the stages of pen testing that AI can impact. As cyber-attacks grow in volume and complexity, artificial intelligence (AI) is helping under-resourced security operations analysts stay ahead of threats. Curating threat [...]
Penetration testing – the highly demanded cyber security service
What is meant by Penetration testing? Penetration testing, also known as pen testing, is the practice of testing a computer system, network, or web application to find security vulnerabilities that an attacker could exploit. Penetration testing can be automated with software applications or performed manually. In any of the ways used, the process involves gathering information about the target before [...]